Who can trigger the Flow
You can create Power Automate flows that get triggered by a http request. Typically they are used for integration between applications so when a http request is received, the flow performs a series of actions. When you create a flow triggered by a http request triggered it creates an unique url that is used to trigger the flow. Within the URL is embedded the SAS, Shared Access Signature, token.
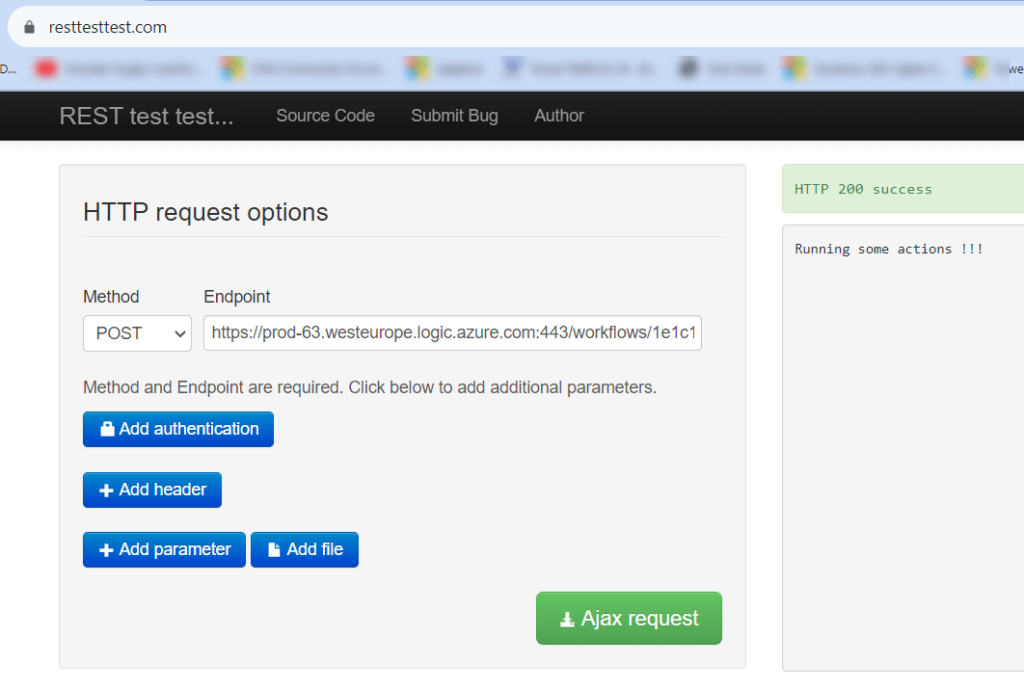
https://prod-11.westeurope.logic.azure.com:443/workflows/28a8632bc1664a8ca91a819e5e188a98/triggers/manual/paths/invoke?api-version=2016-06-01&sp=%2Ftriggers%2Fmanual%2Frun&sv=1.0&SAS token are used to protect access to resources and you should avoid exposing them publicly. By embedding the SAS token directly in the url it means anybody who gets hold of the url can trigger the flow. Generally when used for integrating between applications the url is not widely shared so the the risks are reduced. In scenarios where the flow is being called from a Power App then it may be possible for an inquisitive user to get hold of the the url . If somebody gets hold of the url then they can call it directly.
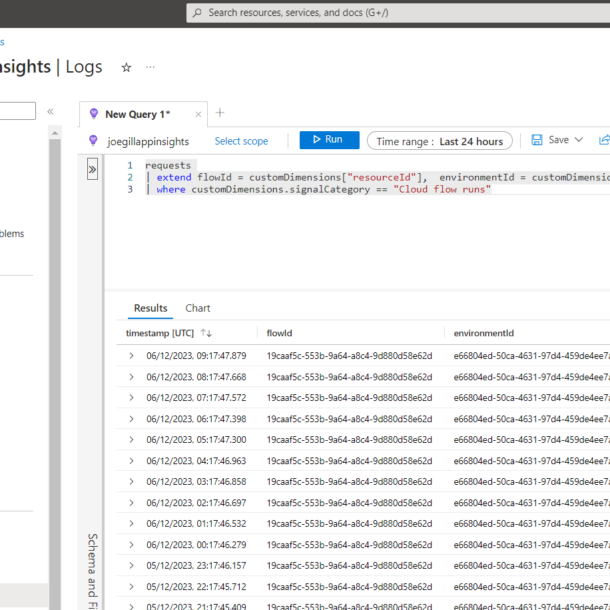
Microsoft have recently taken steps to tighten this up. Now when you create or edit a http request flow you get the options to select “Who can trigger the flow”.
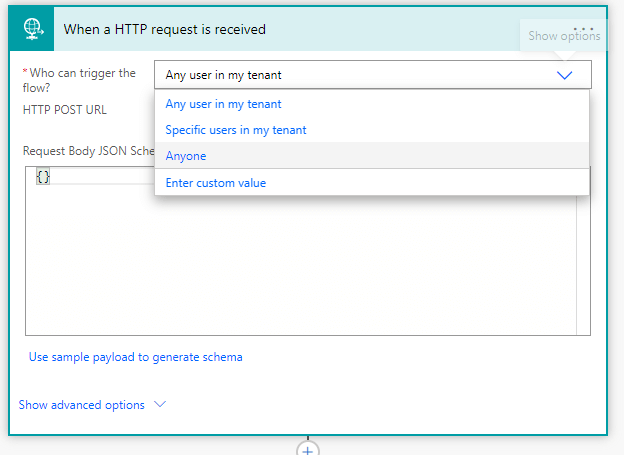
If you select Anyone then your flow url gets created with an embedded SAS token. If you select one of the other two options then the the SAS token, and the sp and sv parameters, are removed from the url.
https://prod-40.westeurope.logic.azure.com:443/workflows/d6026d52bf83420e9c0a5fa0b15212d3/triggers/manual/paths/invoke?api-version=2016-06-01If you try and trigger that url you will get the following error “The request must be authenticated only by Shared Access scheme”
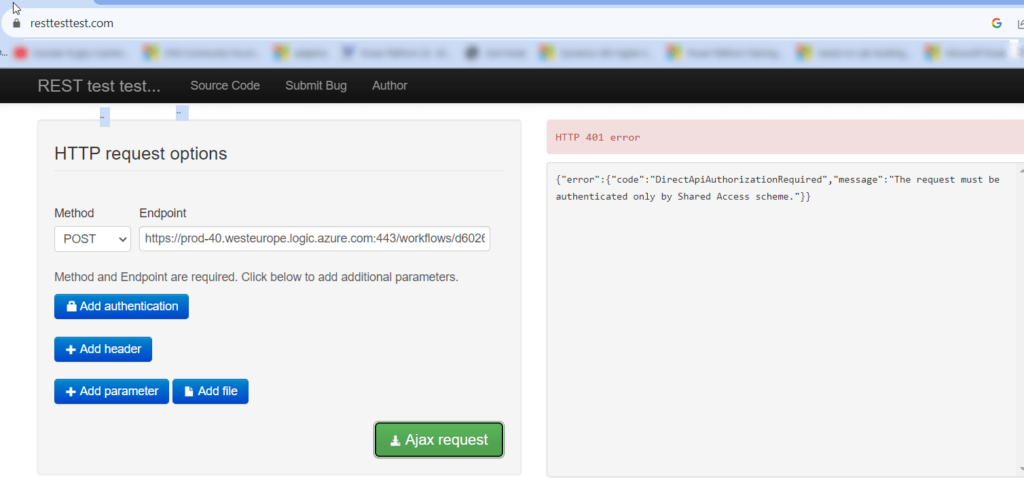
When your flow is configured for “Any user in my tenant” or “Specific users in my tenant” it is restricted to been triggered by authenticated users. In this mode you need to pass a bearer token in the header of the request to trigger the flow. It is more complicated but definitely more secure. Details here